7, Nov 2023
Commvault Appoints Former DOD CNO Analyst and Master Operator Alex Janas as Field Chief Technology Officer, Security
India – November 07, 2023 – Commvault ®, an enterprise data protection leader for today’s
Global Businesses announced that veteran security leader Alex Janas has joined the company
as its new Field Chief Technology Officer overseeing security. With Janas’ appointment,
Commvault is doubling down on its commitment to redefine data protection and deliver cyber
resilience with industry-leading threat detection and rapid recovery capabilities.

“The line between IT operations and security operations is blurring, creating an IT collision of
new vulnerabilities that enterprises need to properly control,” said Rahul Pawar, CTO, Global
Services and Solutions, Commvault. “Alex’s experience going head-to-head with the toughest
cyber threats out there gives us the invaluable insight to develop an offensive security posture
and help keep our customers safe from these ongoing, pervasive autonomous threats.”
Janas comes to Commvault with nearly 20 years of private sector cybersecurity experience, as
well as offensive security skills he developed as an Analyst, Operator, and Technical Director
while working at the National Security Agency. He is a proud recipient of the Master Operator
designation, a prestigious honor bestowed upon a select cadre of Computer Network Operations
(CNO) personnel. His career stands as a testament to his deep expertise, unwavering
commitment to national security, and protection of the private sector while leading and
mentoring other experts in the continually evolving field of cybersecurity.
“The rapidly evolving threat landscape forces defenders to react and respond on their
adversaries’ timetable and magnitude,” said Janas. “To effectively challenge this asymmetry, we
need to create strategies that increase the operational risks and costs for attackers and
minimize the fallout for victims, while also scaling and keeping pace with an attacker’s
adaptations. Being a part of Commvault allows me to apply my offensive cybersecurity
experience to enhance a product that is a pivotal layer in a company’s overarching cybersecurity
strategy.”
- 0
- By Rabindra
6, Nov 2023
On2Cook adjudged the best emerging food tech of the year
New Delhi,6th Nov 2023: The World’s fastest cooking device On2Cook, an invention that could bring about profound changes in the cooking industry, has been adjudged the ‘Best Emerging Food Tech of the Year’. The invention by Sanandan Sudhir, which has created waves at multiple international events and was endorsed by hundreds of chefs & culinary experts globally, bagged the honor at the prestigious Food Connoisseurs India Awards – South India Edition 2023, the most influential business-to-business F&B event presided over by changemakers and top leaders in the HoReCa space.

“On2Cook is an invention with the potential to completely transform the food industry, as much as life in a normal household. This award is dedicated to the whole On2Cook team, for its passion, creativity, and dedication to excellence. We are elated that the AI-based combination cooking appliance is already disrupting the food-tech and cooking segments, and we cannot wait to transform every kitchen around the globe,” said On2Cook inventor Sanandan Sudhir expressing his happiness on the remarkable feat.
Notably, On2Cook has also been included in the Forbes DGEMS 2023 list among 200 select companies with global business potential. Speaking about the same, Sanandan added that he envisions On2Cook as India’s gift to the world and such stepping stones are always a shot in the arm for us.
On2Cook has previously won several prestigious awards globally such as the iF Design Award, the British Invention Show – Diamond Award for Best International Invention, and the Most Celebrated Invention at CES, Las Vegas 2022. The smart cooking device, which combines induction/flame and microwave cooking, initially made its mark in the grand finale of Shark Tank India Season 1. Less than a year ago, On2Cook had secured seed funding worth Rs 17 crore, at a valuation of the same INR 100 crore that was ironically rejected by the Sharks on the television show.
28, Oct 2023
VisionTechFest’s TechThon to Spark Industry-Academia Synergy in India

Bangalore, 28 October 2023 – Visionet, a leading technology solutions provider, introduces TechThon, an innovation-focused event that is a part of VisionTechFest 2023. Designed to bring academia and industry closer together, TechThon focuses on fostering the next generation of tech innovators. Forming a key component of the VisionTechFest – TechThon will offer a unique platform tailored for university students to showcase their innovations in an industry-oriented setting.
The event aims to empower and equip students with essential technical skills needed to pursue careers in technology and innovation. Through real-world exposure and opportunities for mentorship, the platform will allow them to nurture their potential and catalyse their journey towards becoming tech leaders of the future.
Among the key highlights of VisionTechFest’s TechThon, is that the platform has attracted an overwhelming response from students across the country. Out of the 662 teams that registered, an impressive 60 teams have been shortlisted to advance to the upcoming rounds of this exciting event.
The majority of the students and teams participating at the TechThon will represent prominent institutions such as The Oxford College of Engineering, Bengaluru, Presidency University, and Vellore Institute of Technology, showcasing the exceptional talent pool present within these institutions.
Sandeep Agarwal, EVP, Visionet expressed enthusiasm for the event, stating, “VisionTechFest’s TechThon offers an unparalleled platform for students to engage with industry leaders, facilitating an enriching exchange of ideas and providing students with invaluable mentorship opportunities that tap into a vast reservoir of knowledge. Through these connections, students not only gain immediate guidance but also the potential for enduring mentorship that can significantly influence their professional journey.”
Dr. Manjunatha, Principal, from New Horizon College of Engineering, Bangalore, adds, “We firmly believe that the synergy between students and the industry extends beyond the mere transmission of knowledge; it represents a dynamic partnership that catalyses the emergence of novel ideas, disruptive technologies, and groundbreaking solutions. These innovations have the potential to reshape the technological landscape of tomorrow. By sowing the seeds for a future where technology not only evolves but thrives on the ingenuity of the youth, we are setting new standards while also opening up exciting new horizons in the tech world.”
Selected students participating in TechThon will receive expert guidance on their projects, helping them refine their ideas and innovations. Additionally, winners will have the unique opportunity to receive Pre-Placement Offers (PPOs) and internships from Visionet, offering them a direct pathway into a promising career in technology.
VisionTechFest’s TechThon is poised to bring about transformative experiences for the students involved, offering them a platform to turn their ideas into reality and gain exposure to the dynamic tech industry.
27, Oct 2023
Artificial Intelligence in Its Many Forms Will Be the Most Important Area of Technology in 2024
India, October 27, 2023 — IEEE, the world’s largest technical professional organization dedicated to advancing technology for humanity, today released the results of “The Impact of Technology in 2024 and Beyond an IEEE Global Study,” a new survey of global technology leaders from the U.S., U.K., China, India, and Brazil. The study, which included 350 chief technology officers, chief information officers, and IT directors, covers the most important technologies in 2024 and future technology trends.
Telecommunications, Manufacturing, and Financial Industries Most Impacted by Technology in 2024
The top five industry sectors that will be most impacted by technology in 2024, according to survey responses, are:
● (41%) telecommunications (as compared to 40% in 2023)
● (39%) manufacturing (as compared to 30% in 2023)
● (39%) banking and financial services (as compared to 33% in 2023)
● (31%) automotive and transportation (as compared to 39% in 2023)
● (31%) energy (as compared to 33% in 2023)
AI will be the Most Important Technology in 2024 – Used in Diverse Ways,
Across the Global Economy
What areas of technology will be the most important in 2024? From over a dozen areas of technology, when asked to select the top three, respondents chose:
● (65%) Artificial Intelligence (AI), including predictive and generative AI, machine learning (ML) and natural language processing (NLP)
● (28%) Extended reality (XR), including metaverse, augmented reality (AR), virtual reality (VR) and mixed reality (MR)
● (24%) cloud computing
Other important technologies in 2024 include 5G (22%), and electric vehicles (20%).
In 2024, AI applications and algorithms that can optimize data, perform complex tasks, and make decisions with human-like accuracy will be used in diverse ways, the study finds. Of top potential applications for AI next year, technology leaders surveyed selected:
● (54%) real-time cybersecurity vulnerability identification and attack prevention;
● (42%) Increasing supply chain and warehouse automation efficiencies
● (38%) aiding and accelerating software development, automating customer service
● (35%) automating customer service
● (34%) speeding up candidate screening, recruiting, and hiring time
● (32%) Accelerating disease mapping and drug discovery
● (31%) Automating and stabilizing utility power sources
Survey participants were asked what percentage of jobs across the global economy in 2024 will be augmented by AI-driven software, and 26-50% of jobs was cited by 41% of those surveyed. Over one-quarter (28%) cited 1-25% of jobs; another 26% cited 51-75% of jobs, and 5% cited 76-100% of jobs.
Benefits of Extended Reality (XR), Digital Twin Technologies, 5G and 6G
According to the IEEE survey, virtual simulations using extended reality (XR) and digital twin technologies to more efficiently design, develop, and safely test product prototypes and manufacturing processes will be important in 2024 (63% very important, 29% somewhat important).
Respondents see 5G benefitting the following areas the most in 2024, including greater benefits to transportation infrastructure and sustainability as compared to 2023.
● (54% in both 2024 and 2023) telemedicine, including remote surgery, health record transmissions
● (46% in 2024 vs. 49% in 2023) personal and professional day-to-day communications
● (46% in 2024 vs. 56% in 2023) Remote learning and education
● (43% in 2024 vs. 51% in 2023) entertainment, sports and live event streaming
● (39% in 2024 vs. 29% in 2023) Transportation and traffic control
● (27% in 2024 vs 25% in 2023) manufacturing/assembly
● (30% in 2024 vs 23% in 2023) carbon footprint reduction and energy efficiency
Close to nine out of 10 of global technologists (88%) agree 6G will primarily be an evolving work in progress in 2024, but will be standardized in the next 3-5 years. In addition, a strong majority (94%) of global technologists agree that the development of communication satellites for mobile connectivity will bring parity to some rural and developed regions globally in 2024.
Don’t Count Quantum Out
Generative AI may continue to dominate the technology landscape, but other technologies such as quantum will have significant, if less-noticed impacts (87% agree, including 51% who strongly agree). Furthermore, 86% of respondents agree, that in 2024 quantum computing will gain the most attention for significantly higher computing power – a trillion times higher than that of today’s most advanced supercomputers, as well as for its application to post-quantum cryptography and cybersecurity.
Technologies that foster sustainability continue to be a priority. A strong majority agree (92% agree, including 54% who strongly agree) that they have prioritized sustainability goals for 2024 and beyond, and any technologies their company implements are required to be energy-efficient and help shrink their carbon footprint.
Cybersecurity Concerns Continue
The cybersecurity concerns most likely to be in technology leaders’ top three in 2024 remain the same as last year: data center vulnerability (43% in both 2024, and 2023), cloud vulnerability (42% in 2024, down from 51% in 2023) and security issues related to the mobile and hybrid workforce/employees using their own devices (41% in 2024, down from 46% in 2023). However, the study finds other cybersecurity concerns will rise in 2024, including ransomware attacks (37% in 2024 up from 30% in 2023), phishing attacks (35% in 2024 up from 25% in 2023), and insider threats (26% in 2024, up from 19% in 2023).
27, Oct 2023
Bad bots use residential IPs to appear human and evade defenses, reveals Barracuda’s Threat Spotlight Report
India, 27th October 2023: Barracuda, a leading provider of cloud-first security solutions, has unveiled a new Threat Spotlight that shows how in the first six months of 2023, bad – or malicious – bots used residential IP addresses to launch attacks without being caught by the security blocks put on known malicious IPs. In many cases, the people who used or were later allocated those IPs ended up in “CAPTCHA hell,” unable to pass checks from Google or Cloudflare because their IP triggered a red flag as having been used for malicious activity.
Bots are software programs that move around the web performing automated tasks like search engine crawling. Barracuda researchers track the prevalence and behavior of good and bad bots from year to year.
Data for the first half of 2023 shows that nearly half (48%) of total global internet traffic was made up of bots, and most of this was down to bad bots. These complex computer programs are designed to cause mischief and harm, at speeds and volumes that human attackers couldn’t match.
And while in 2021, the bad bot landscape was dominated by swarms of “retail bots,” sent out to hunt for scarce and sought-after sneakers and toys to resell at a profit, in 2023, bad bots are often being used for more advanced attacks.
Armed with millions of common username and passwords, the bad bots are being sent out across the internet with the aim of compromising email accounts – particularly those they can reach through vulnerable application programming interfaces (APIs) – by bashing them with countless combinations of usernames/passwords until they get the one that works.

APIs are a growing target for cyberattack because they are relatively under-protected and used extensively for automated processes and communications. Examples of applications that use APIs to access emails and inboxes include email marketing applications that send and track bulk or personalized emails to potential or existing customers, as well as applications to manage, verify, and automate emails.
“For the organizations targeted by these bots, a combination of under-secured APIs, weak authentication and access policies, and a lack of bot-specific security measures – such as limiting the volume and speed of inbound traffic leave them vulnerable to attack,” said Tushar Richabadas, Principal Product Marketing Manager, Applications and Cloud Security at Barracuda. “Organizations can be overwhelmed due to the sheer number of solutions required to stop bots, but the good news is that solutions are consolidating into Web Application and API Protection (WAAP) services that identifies and stops bad bots.”
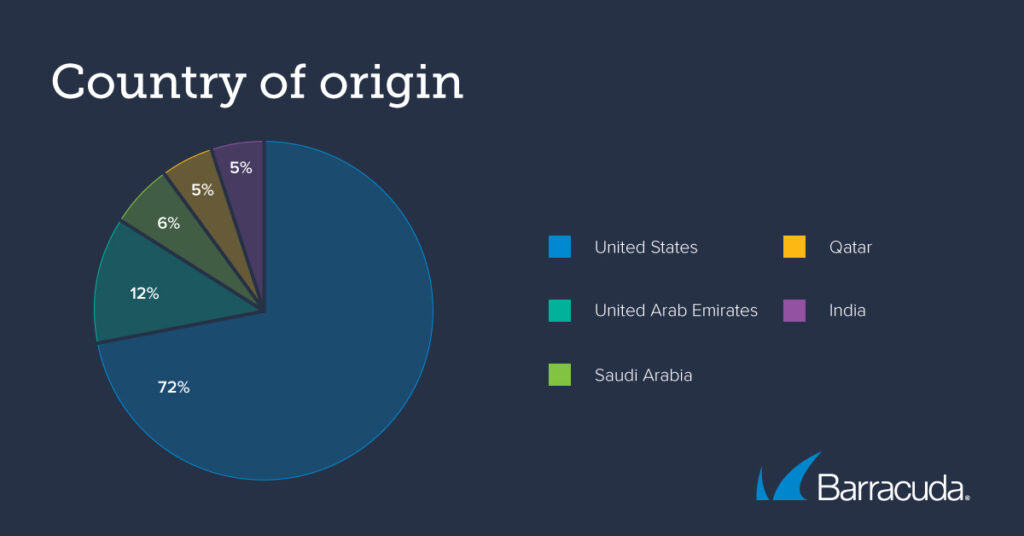
The research also shows that in the first half of 2023, North America was the source of 72% of bad bot traffic. Roughly two-thirds (67%) of bad bot traffic came from hosting providers, including the two large public clouds: AWS and Azure, which skews the geographic data toward North America. The next most prevalent regions are the United Arab Emirates (12%), Saudi Arabia (6%), Qatar (5%), and India (5%).
19, Oct 2023
Newest Ransomware Trend: Attackers Move Faster with Partial Encryption

On Wednesday morning, May 3, 2023, security personnel with the City of Dallas were horrified when their security software alerted them that they had likely become the target of a ransomware attack. Multiple servers across a range of departments were affected: 911 dispatchers, courts, and police services couldn’t use their computers for days.
It later emerged that sensitive data had been stolen—800,000 files containing full names, home addresses, Social Security numbers, dates of birth, and the health and insurance data of at least 30,000 city employees and other individuals. Two weeks later, the Royal ransomware group, which took responsibility for the attack, threatened to release the information. In particular, police officers and others whose data had been stolen feared the data could fall into the hands of violent offenders who might try to retaliate.
The City of Dallas wasn’t the first government to be hit by ransomware—or the first ransomware attack where lives could have been lost. The Royal ransomware group was originally part of the Conti group, which previously took credit for bringing the entire Irish healthcare system to a halt in 2021.
One of the reasons Royal was able to strike so quickly and effectively in Dallas is that they took advantage of today’s fastest-growing ransomware trend: partial encryption.
The term “partial encryption” may sound more benign at first than traditional attack strategies, since theoretically less damage is being done. However, in fact, it’s no less devastating to organizations that find themselves under attack.
In this post, we’ll explore the emergence of partial encryption as a strategy to make cybercrime even more profitable, which industries are at risk, and finally, a few key steps to help you protect your business.
Why Do Attackers Choose Partial Encryption for Ransomware Attacks?
Encryption is a tried and true strategy for malware actors. Malware within the victims’ systems leaves their data in place but completely inaccessible. Attackers then demand a price to unlock the data so victims can resume business as usual. In a second-tier strategy, in the event that victims refuse to pay, attackers can still make money by selling the compromised data.
Based on this model, ransomware has become big business over the last decades. And like all big businesses, attackers are always seeking to optimize their operations and find more efficient, cost-effective ways to achieve the same or better results.
Encryption in particular can be very time-consuming, especially for large amounts of data. This has led attackers to seek more efficient, effective ways to render victims’ data inaccessible unless they pay the ransom.
Partial encryption, also known as intermittent encryption, has emerged as just one example of increasingly sophisticated attack tactics, often in readily available off-the-shelf ransomware products that are openly sold on the darkweb much like traditional software.
Rather than encrypt the entire compromised system, partial encryption does just that: It encrypts a portion of the victim’s files either at random, encrypting a predetermined percentage of the data, as Royal ransomware does, or encrypting only the most important files, as determined by fingerprinting: financial documents, photos, and personal information. Ransomware can also selectively encrypt files related to a particular project or task, bringing it to its knees until payment is made.
For attackers, the advantages of partial encryption over complete encryption are clear:
- Speed– Faster and less resource-intensive than traditional encryption, attackers can finish partial encryption before victims even notice the intrusion.
- Complexity– Because only some data is encrypted, it’s harder for victims to restore data from backups, increasing the odds that they will simply pay the ransom.
- Less detectable- Automated scanners might not notice the smaller-scale modifications made by partial encryption while compromised systems may not behave as erratically as completely encrypted systems, triggering fewer alerts. Royal ransomware is particularly insidious because it not only uses partial encryption but also a multithreaded model, another increasingly popular strategy. In a single attack, there is only one ransomware process; a multithreaded attack uses multiple CPU cores to encrypt files simultaneously. This can quickly overwhelm the available processing power and make the attack more difficult to stop; even if one or two child processes can be stopped, the others will continue to encrypt files. This means that multithreaded ransomware attacks can be very destructive.
Even more frightening, today’s attackers have begun using a “triple extortion” strategy. With a double extortion strategy, as previously described, attackers not only hold the encrypted drives for ransom, they threaten to release or sell encrypted data if the organization does not pay. For the victim, this means that even if files can be restored from a backup, they must still pay to avoid data leakage.
However, a triple extortion strategy unfolds, as the name suggests, over three stages:
- Infiltrate and encrypt. Attacker profits when the initial victim pays the ransom.
- Exfiltrate and threaten to sell. Attacker can profit from the sale of data.
- Ransom third parties. Attacker demands ransom from third parties whose data has been stolen, such as patients or employees; they may also threaten the organization or its partners with distributed denial-of-service (DDoS) attacks.
However, whether ransomware attackers use one of these new strategies or a more traditional approach, the goal is always the same: to extort money. And the truth is that even after paying up, few organizations can reconstruct 100% of their compromised data.
Therefore, the best defense against today’s ransomware is thwarting attacks altogether.
Who Are the Attackers?
When combating ransomware, it’s important to understand who you’re up against. Today’s ransomware attackers are far from the stereotypical hooded criminal-in-a-basement, although that may have been who was behind very early ransomware, 10 to 15 years ago. Attackers back then would use broad-scale, fairly obvious, and generally imprecise attacks that succeeded in bringing in small amounts of money.
Today, like all technology industries, ransomware has matured beyond these modest origins. Ransomware gangs have formed larger-scale enterprises and brought talented developers on board to research and implement increasingly sophisticated techniques, methods deployed against wealthier targets to reap the highest rewards.
And these illicit enterprises have found safe havens in places like Russia, Asia, and Eastern Europe. Today, in addition to these large and highly professional enterprises, hostile governments and other nation-state entities are using ransomware for nation-level intelligence-gathering operations. And beyond literal warfare, ransomware has become a powerful digital weapon in corporate warfare as well.
There are numerous hacking groups out there, but a few leading ones deserve a mention.
- Chernovite – A likely nation-state group and the developer of Pipedream, U.S. law enforcement has called this modular industrial control system (ICS) toolset a “Swiss army knife” for attacking utility companies (electricity, water, natural gas) in the U.S. and Europe.
- Bentonite – An opportunistic group affiliated with Iranian hacking groups Phosphorus and Nemesis Kitten, Bentonite leverages known vulnerabilities in maritime oil and gas, government, and manufacturing infrastructure.
- ALPHV/BlackCat– BlackCat is a relatively new ransomware group that popped up in late 2022. It is known for its sophisticated encryption and ability to target a wide range of organizations. It is believed BlackCat is operated by a group of Russian-speaking cybercriminals and is known to use intermittent encryption via customizable byte-skipping patterns.
- Hive– Before being brought down by the U.S. FBI, German law enforcement, and the Dutch National High-Tech Crime Unit, this ransomware group had extorted over $100M by terrorizing healthcare organizations, schools, and public infrastructure worldwide. While the investigation is ongoing, Hive is believed to have ties to the Kremlin.
Attacks
In just the first half of 2023, 48 ransomware groups including these and others—such as Ryuk, Medusa, Play, LockBit3, and many more—have breached over 2,200 victims, 45% of whom are in the U.S.
These groups use two main vectors to introduce ransomware: through software vulnerabilities, which are unintentional weaknesses or flaws in applications or code libraries that can go unpatched for years, and social engineering techniques, such as phishing. Attacks often combine these two strategies, or use variations such as callback phishing attacks, which are commonly used by the Royal ransomware group, the group behind the Dallas attack.
Regardless of how individual groups operate, and which encryption technologies they’re using, the consequences can be dire, as in an August 2023 ransomware attack on two Danish cloud hosting companies that resulted in the total loss (to encryption) of all customer data. An unidentified attack group demanded 6 bitcoins in ransom (approx $155,000 as of this writing), an amount CloudNordic was unable to pay; the company has since shut down its operations.
What Industries Are Most at Risk?
There are several sectors that find themselves frequently targeted by ransomware attacks.
Healthcare– Medical IT departments are both the most obvious and the most sensitive target since lives are most clearly on the line. When the Rhysida ransomware group, which had gained notoriety for its attack on the Chilean army, attacked Prospect Medical in August of 2023, the company—which operates 16 hospitals and numerous clinics all over the U.S.—was forced to use paper charts until systems could be restored. Healthcare data is both sensitive and valuable; it also features a large threat surface and a wide range of device types, including a mix of old and new technologies. This type of environment is hard to securely administer and update. This is especially true of medical IoT devices, which are often not built securely by design. Finally, healthcare organizations are historically more likely to pay ransoms compared with other industries, specifically so that life-saving operations will not be interrupted. The year 2022 brought an average of 1,426 attempted breaches per week per organization in the healthcare industry, a 78% year-over-year increase. There was also a distinct uptick in mortality following a cyber attack, although attributing deaths directly to ransomware is almost impossible due to the complexity of the events involved. Deaths connected with ransomware attacks can come about due to slowdowns, meaning delays in important surgeries and other care, as well as a lack of electronic health records, leading to a higher chance that patients will be given the wrong medication or an incorrect dose. In a recent Ponemon study of healthcare IT professionals, almost half (45%) said ransomware led to increased complications from medical procedures, up from 36% just a year earlier.
Higher Education– Just as school was starting back in September of 2021, Howard University, one of the U.S.’s five largest historically black colleges and universities, was forced to cancel classes due to a ransomware attack. Attacks against higher education institutions are on the rise, with at least eight reporting ransomware attacks since December 2022. Why are attackers targeting these schools? Colleges and universities are seen as attractive targets because they hold valuable data and their IT departments are often understaffed and outdated, with limited security resources. Educational institutions are also considered slower to recover than other sectors. Despite the fact that 64% of higher education institutions experienced attacks in the past year, many are still unwilling to discuss these incidents due to the negative influence they may have on a school’s reputation. Unfortunately, because of this silence, others in the sector may not realize that they are at risk—further perpetuating the cycle.
Manufacturing– In February of 2023, MKS Instruments, a little-known U.S.-based supplier to major players in the semiconductor industry, woke up to every manufacturer’s worst nightmare: a ransomware attack. Hackers compromised production and business systems, leading to predictions of $200M in losses from the attack. But the worst may be yet to come: Employees have filed a class action suit, claiming that the company did not adequately protect their sensitive personal data. Attacks on semiconductor companies have continued: Taiwan Semiconductor Manufacturing Company (TSMC) itself, the world’s largest chip manufacturer, was hit by the LockBit ransomware group in June 2023. The group demanded $70M, adding: “In the case of payment refusal, also will be published points of entry into the network and passwords and logins company.” But the semiconductor sector is not alone; almost every major field of manufacturing is being targeted. In fact, the manufacturing sector has been the industry most heavily hit by ransomware. The primary vector is unpatched vulnerabilities, particularly in industrial control systems. Manufacturers may also be more likely to pay ransoms to avoid production disruptions and financial losses, as well as devastating repercussions up and down the supply chain.
Tips to Protect Your Business From Today’s Sophisticated Ransomware
Although these three industries are among the most frequently targeted, attacks like the one in Dallas, the cloud providers in Denmark, and other victims profiled above reveal the broader truth that any organization storing sensitive data is at risk today, from financial services and insurance to retail and logistics.
That’s especially true now, with partial encryption likely to increase in popularity as ransomware gangs study one another’s techniques. As more and more adopt this hyperefficient technique, they will find it easier and more effective than ever to steal your assets and avoid interception. So regardless of your industry, now is the time to take a few important steps to protect your organization from ransomware.
Inventory Assets– All comprehensive security strategies begin with a comprehensive assessment of what you need to protect, including OT assets that may be the weakest link in your organization.
Stay on Guard 24/7– When it comes to ransomware attacks, hackers usually take advantage of times when people are not as vigilant. In the past year, most breaches have occurred on weekends and holidays.
Patch, Patch, Patch– Keep up to date with a rigorous patching regimen, since known vulnerabilities are a popular attack vector. Also, automate patching wherever possible.
Watch for Pre-Ransomware– Trojan malware infections like Trickbot, Emotet, Dridex, and Cobalt Strike should be dealt with immediately, as these can all be used to let ransomware in the door; similarly, taking steps to prevent phishing and train users can help foster a culture of security.
Get Backed Up– Store multiple copies of data in different locations (cloud, on-premises, and physical locations), and establish a backup testing regimen. Remember, never attach an uninfected backup to an infected computer. This could spread the ransomware to the backup and make it impossible to recover your data.
Minimize the Blast Zone – Reduce the impact of a potential attack with security measures such as strong user authentication and network segmentation to limit the radius of an attack’s spread.
It is important to note that none of these measures can provide complete protection. And particularly in light of the fact that partial encryption is notoriously difficult to detect, your best bet is a comprehensive anti-ransomware solution.
Check Point Harmony: The Industry’s Best Prevention
The best way to keep your organization safe is effective threat prevention with an organization-wide anti-ransomware solution that uses up-to-the-minute threat intelligence data along with advanced algorithms that work automatically in the background, around the clock.
Check Point Harmony is the first unified security solution that protects users, devices, and internet connections from the most sophisticated attacks, including phishing, zero-day ransomware, and more. It also ensures that users only have access to the applications they need, which helps reduce the risk of data breaches.
Check Point Harmony delivers peace of mind with a total, holistic defense against malware:
- Constantly monitors for ransomware-specific behavior
- Detects threats fast so teams can act quickly to minimize harm
- Identifies illegitimate file encryption; signature-less to detect new attack types
- Uses forensic analysis to detect and quarantine all elements of a ransomware attack
- Automatically restores encrypted files from snapshots to ensure business continuity
Check Point Harmony is prevention-focused, stopping attacks before they become a threat to your organization. Powered by
real-time threat intelligence through Check Point’s ThreatCloud AI and backed by the industry-leading Check Point Research
team, Check Point Harmony gives you today’s best security, hands down.
19, Oct 2023
Fintech’s Cloud Computing Frontier: Scaling, Securing, and Innovating

Financial services organizations can now access, store, and analyze data more securely and effectively than ever due to cloud computing. This has provided an ideal foundation for fintech companies to create game-changing products, services, and technology that have altered the financial environment.
By 2025’s end, the total value of the worldwide fintech market is forecast to reach $124.3 billion, expanding at a CAGR of 23.84% throughout that period. The financial technology industry increasingly relies on cloud computing services to meet the needs of its customers in the commercial and consumer sectors.
Why, therefore, do FinTech companies need to use cloud computing? Let’s see the impact of cloud computing on organizations and consumers in the fintech sector.
Role of Cloud Computing in Fintech
The advent of cloud computing in financial technology has dramatically expanded the industry’s potential and altered the financial sector’s requirements. LogicMonitor Research shows that by 2025, 87% of businesses will have accelerated cloud migration.
Cloud computing has made fintech more widely available, safer, and adaptable to different users’ specific requirements. Fintech cloud computing is expanding steadily, although cloud applications are still in their early days. Furthermore, 22% of fintech apps are currently cloud-based. However, this creates ample space for development and innovation.
Importance of Cloud Computing in Fintech
Financial data is increasing at an exponential rate. With the help of cloud computing, FinTech companies can safely and reliably handle and retain customer data. In addition, it lets companies use cutting-edge approaches to banking, money transfers, and fraud detection.
According to Statista’s global data report, in 2021 alone, more than 79 zettabytes of data were created, but only 10% was original, with the remaining 90% being replicated. Cloud-based solutions are essential because of the massive amount of data in a fintech business. By 2025, we will have created more than twice as much data, according to Statista’s forecasts (181 zettabytes).
The complexity of data, the volume of data being handled, and end users’ expectations have all made data integration an absolute must. The only way to keep up with the expanding computing demands of a dynamic business while guaranteeing unrivalled dependability and giving it a competitive edge is to use the cloud.
The Role of Cloud Computing in Modern Lending
In the current commercial lending sector, cloud-based solutions replace manual procedures with cloud automation predicated on speed, scalability, and ease of use for loan origination and administration needs.
With banks showing a greater willingness to lend to consumers, now is the time to accelerate digital transformation and meet the needs of the next generation of enterprises on the cloud. Let’s examine the benefits of cloud computing for lenders and companies alike.
Scalability and agility
The capacity to expand operations as needed is a driving force behind the lending industry’s growth. In addition, with cloud computing, there is no longer any need for backups, updates, or repairs to the underlying infrastructure. It enhances customer experience, innovation, and productivity, making learning outcomes scalable.
Enhanced Security Measures
Maintaining data integrity by blocking unauthorized access is crucial to cloud storage. Many cloud systems alert administrators of discrepancies by comparing the data to the previous excellent condition. Banks can reduce security threats via thorough audits, multi-factor authentication, and restricted IP address lists by working with a reliable cloud service provider.
Cost Optimization
By using cloud computing services, organizations can reduce the need for expensive software installations, such as on-site dedicated chat servers. Businesses can cut their IT expenses by paying for just the services they need at the right time using software-as-a-service (SaaS) solutions like ATS tracking systems and customer relationship management tools.
Regulatory Compliance
The cloud creates the perfect environment for compliance by anticipating and resolving regulatory demands and identifying and managing risk gaps. Lenders may rest assured knowing that any data they submit is error-free and can be retrieved quickly and easily whenever needed. In addition, businesses will not face any compliance-related fines.
The cloud-based solution is a game-changer for the finance sector. Fintech companies can swiftly roll out new services and keep up with the competition through improvements in scalability, security, user experience, time to market, and data analytics.
19, Oct 2023
HCLTech’s IoT device management solution wins Future Digital Award 2023
NOIDA, India, Oct 19, 2023: HCLTech, a leading global technology company, announced that its IoT solution, which helps enterprises remotely monitor and securely manage a diverse assets ecosystem, won the Future Digital Award 2023 in the ‘Best IoT Device Management Platform’ category.
By enabling a real-time, single-pane view of IoT/operational technologies (OT) across a multi-vendor and heterogeneous device environment, the solution helps enterprises preempt and mitigate costly downtimes. Solution highlights include customizable reports and alerts, standardized workflow, secure access controls, and an efficient user interface.
“This recognition from Juniper Research validates HCLTech’s commitment to building and delivering cutting-edge solutions that help supercharge progress for our customers,” said Sukant Acharya, Executive Vice President, IoT and Industry NeXT, HCLTech. “Developed by IoT WoRKSTM, HCLTech’s IoT and Industry NeXT business unit, our IoT device management solution offers enterprises a smart and secure way to configure, manage, monitor, predict, alert and troubleshoot the growing number of connected devices they rely upon for their operations.”
Since 2008, Future Digital Awards by Juniper Research have been conferred on technology companies that are at the forefront of innovation in their respective fields. The award recognizes companies that deliver imaginative, innovative products or services that have the potential to disrupt their ecosystems and provide significant benefits to their clients.
16, Oct 2023
Showcasing Parametric Designs In Shaping a Sustainable Future

Kolkata, 16th October 2023: In an endeavour to push the boundaries of design innovation, ABID (Association of Architects, Builders, Interior Designer and Allied Trade) launched its dynamic programme on Parametric Designs, aimed at discussing the application of Artificial Intelligence (AI) in architecture and interior designing.
Eminent architects Mr. Sushant Verma, Co-founder & Design Head, rat[LAB], Mr. Monish Siripurapu, Founder, Ant Studio, Mr. Shridhar Mamidalaa, Founded, Sri Design Lab, shared their knowledge and expertise on the principles and application of Parametric designs in Architecture and interiors.
The event included a panel discussion on ‘Parametrics for Sustainable Future’, addressed by eminent architects from the city – Mr. JP Agrawal, Director, Agrawal & Agrawal Architects, Mr. Kamal Periwal, Founder, Maheshwari & Associates, Mr. Vivek Singh Rathore, Director, Salient Design Studio.
The program will also include felicitations and the presentation of student awards, recognizing outstanding achievements in the field of design.
“ABID, the driving force behind this seminar, stands at the forefront of architectural advancement, with a mission to foster creativity and innovation in the architectural community. The organization is committed to empowering architects and designers with the knowledge and tools to shape a sustainable future,” Mr Kamlesh Agarwal, President of ABID said.
An exhibition showcasing the practical applications of Artificial Intelligence in conjunction with Parametric Design was also showcased during the event for the participants of the event. This exhibition offered attendees a first-hand experience of the cutting-edge technology driving innovation in the field of design.
Convenor of the event Ms. Deepa Agarwal, who is also an accomplished architect with a passion for pushing the boundaries of design has been instrumental in curating the programme.
16, Oct 2023
HCLTech recognized as a Leader in Everest Group’s ACES Automotive Engineering Services PEAK Matrix Assessment 2023
NOIDA, India, Oct 16, 2023 — HCLTech, a leading global technology company, has been recognized as a Leader in Everest Group’s ACES (Autonomous, Connected, Electric and Shared) Automotive Engineering Services PEAK Matrix® Assessment 2023.
According to Everest Group, HCLTech has an extensive portfolio of IP around telematics platform, battery management systems and LiDAR (Light Detection and Ranging), supported by a strong and growing ecosystem of partners.
“HCLTech has a multitude of offerings around Advanced Driver Assistance System (ADAS), crash assistance systems, battery management systems, infotainment, telematics and charging solutions,” said Nishant Udupa, Practice Director at Everest Group. “These offerings are further backed by investments in developing solutions, establishing labs and CoEs and a robust partnership network in the aforementioned areas. Clients have appreciated HCLTech’s flexibility to adapt to project requirements, commercials, their access to wider talent pool and strong domain knowledge in the ACES space. The acquisition of ASAP has further helped HCLTech to strengthen its capabilities in areas such as e-mobility and autonomous driving. All these factors have helped HCLTech emerge as a Leader in Everest Group’s ACES Automotive Engineering Services PEAK Matrix® Assessment 2023.”
“In the rapidly evolving automotive engineering services sector, HCLTech has emerged as a global Leader, distinguished by our multi-vertical expertise and extensive experience in traditional and digital engineering. With the addition of ASAP Group, a leading German automotive engineering service provider, we have further strengthened our position and influence in the market, reaffirming our diverse portfolio and our commitment to deliver exceptional value to our clients. With the ACES segment all set to transform the future of mobility, we are proud to be associated with the leading automotive companies in their transformation journey to make transportation safer, more efficient and sustainable,” said Hari Sadarahalli, Corporate Vice President, Engineering and R&D Services, HCLTech.
HCLTech is uniquely positioned to partner with enterprises seeking to leverage digital technologies to transform their business. As the automotive industry undergoes a radical transformation, HCLTech remains at the forefront, driving innovation and shaping the future of mobility.